Create Secure Software
With our industry-leading assessments and learning platform
Level Up Your Software Security
Across Your Organization
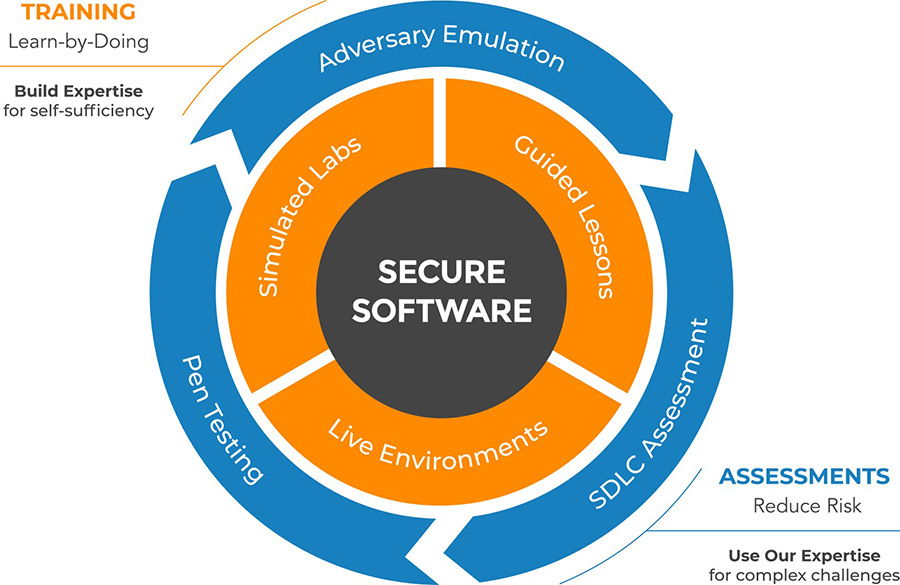
Transform Software Security
Eliminate skills gaps, mitigate risk, achieve compliance and drive productivity with secure code training and assessments.
We’ve helped some of the best protect their brand








How we Help: We Empower You
Robust learning solutions with a twist.
Delivering expertise, real brain power, and employee competency to add to your arsenal.
The Software Security Challenge: A Unique Perspective
The lines of responsibility are blurring and both experts and everyday staff are rising to the challenge.
A Functional Approach to Software Security
Builders
Operators
Defenders
Explore how your interaction and role in software security impacts the trajectory and
maturity of your whole company – and how we can help companies meet the challenge.
Experience Security Innovation
Long history
20+
20+ years maturing the art of software security
Proven Results
3M+
over 3 million individuals boosted to the next level
Respected Experts
30%+
we work with over 30% of the Fortune 100 companies
Always Out Ahead
6X
Gartner MQ


